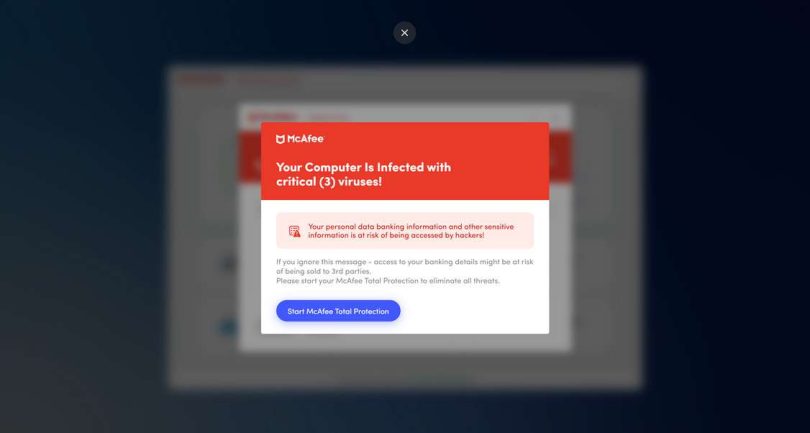
Viruses and malware files have been detected pop-up scams are becoming increasingly common, and it’s essential to be aware of them to protect your digital security. In this article, we will explore the different types of viruses and malware files, how they work, and what you can do to avoid falling victim to pop-up scams.
Viruses and malware files are designed to harm your computer or mobile device, either by stealing sensitive information, installing additional malware, or disrupting your normal operations. There are many types of viruses and malware, each with its own unique characteristics and capabilities. Some of the most common types of malware include Trojans, worms, and spyware.
Trojans are one of the most common forms of malware, and they are designed to infiltrate your computer or device without your knowledge or consent. Once a Trojan is installed, it can give hackers remote access to your device, allowing them to steal sensitive information, install additional malware, or disrupt your online activities. Trojans can be spread through email attachments, software downloads, or infected websites.
Worms are similar to viruses, but they are able to propagate themselves without the need for a host program. They can cause widespread damage by spreading from one computer to another, often without the user’s knowledge or consent. Worms are often spread through email attachments, instant messaging apps, or infected removable media.
Spyware is designed to collect sensitive information about your online activities, such as your browsing history, passwords, and credit card numbers. Spyware can be spread through email attachments, software downloads, or infected websites.
It’s essential to be aware of the dangers of viruses and malware to protect your digital security. Here are some tips on how to avoid falling victim to pop-up scams:
1. Install a reputable anti-virus software and keep it up to date. This will help detect and remove any malware that your computer may have detected.
2. Be cautious when clicking on links or downloading software. Make sure you only download software from trusted sources, and be wary of pop-up ads or offers that seem too good to be true.
3. Use strong passwords and enable two-factor authentication whenever possible. This will help prevent unauthorized access to your accounts and devices.
4. Keep your operating system and software up to date. Regular updates often include security patches and fixes for known vulnerabilities.
5. Use a reputable firewall to block unauthorized access to your device. This will help protect your device from unauthorized access and prevent malware from spreading.